You can ensure that people only sign in to Webex App using accounts from a predefined list of domains. Use a proxy server to intercept requests and limit the domains that are allowed.
You can use the following steps as guidelines to configure your web proxy server.
Before you begin
-
You must install a proxy server that can perform Transport Layer Security (TLS) interception, HTTP header insertion, and filter destinations using fully qualified domain names (FQDNs) or URLs.
The following are tested Web proxy servers and the detailed steps are provided below to configure these proxy servers:
-
Cisco Web Security Appliance (WSA)
-
Blue Coat
-
-
To ensure you have the ability to do HTTP header insertions in an HTTPS connection, TLS interception must be configured on your proxy. See the information about proxies, in Network requirements for Webex services, and ensure you meet the requirements specific to your proxy server.
| 1 |
Route all outbound traffic to Webex through your web proxy servers. |
| 2 |
Enable TLS interception on the proxy server. |
| 3 |
For each Webex request: People who attempt to sign in to Webex App from an unauthorized account receive an error.
|
You can use Cisco Web Security Appliances (WSA) proxy server to intercept requests and limit the domains that are allowed. Add custom headers in WSA and these headers are applied to outgoing Transport Layer Security (TLS) traffic to request special handling from destination servers.
| 1 |
Access the WSA CLI. |
| 2 |
Enter 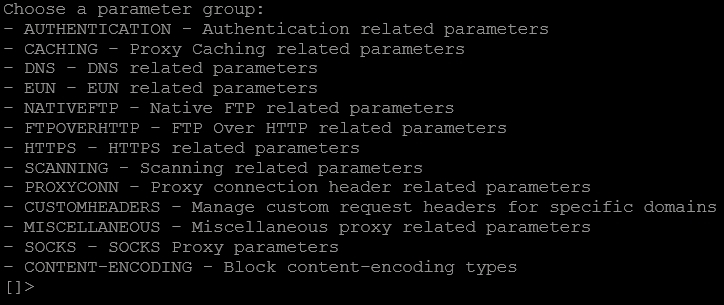
|
| 3 |
Enter 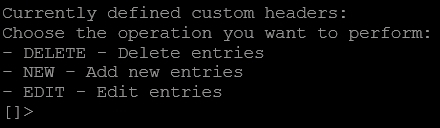
|
| 4 |
Enter 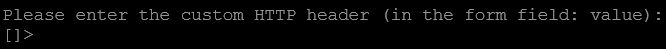
|
| 5 |
Enter Where EXAMPLE.COM is the domain to use this header with. 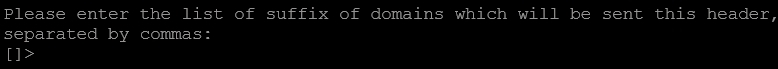
|
| 6 |
Enter 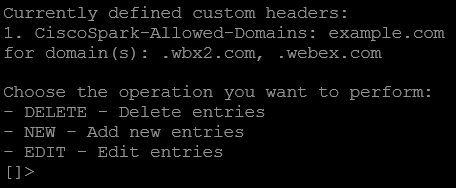
|
| 7 |
Select Return. 
|
| 8 |
Select Return and enter |
| 1 |
In the Visual Policy Manager, select . |
| 2 |
Select . |
| 3 |
Click Install Policy. |

